#### [[The Illustrated Guide to Transport Layer Security (TLS)]]
---
TLS 1.3: https://tls13.xargs.org/ - other cool byte-level explanations like QUIC here too.
https://tls.ulfheim.net
This shows a byte-by-byte description of what happens with a TLS connection.
Basically modulo arithmetic to exchange secret key without it hitting the wire. The large prime factorization (discrete logarithm) problem is considered hard.
Diffie Hellman Algorithm
The purpose of this protocol is to allow two parties to set up a shared secret key over an insecure communication channel so that they may exchange messages. Alice and Bob agree on a finite cyclic group G and a generating element g in G. We will write the group G multiplicatively.
1. Alice picks a prime number p with the base g, and an exponent a to generate a public key A.
2. A = g^a mod p
3. (g, p, A) are made public and a is kept private.
4. Bob picks a prime number p, base b (sic g), and an exponent b to generate a public key B.
5. B = g^b mod p
6. (g, p, B) are made public and b is kept private.
7. Bob using A generates the shared key S.
8. S = A^b mod p
9. Alice using B generates the shared key S.
10. S = B^a mod p
Thus the shared key S is established between Bob and Alice.
However, it can be susceptible to MITM like this: 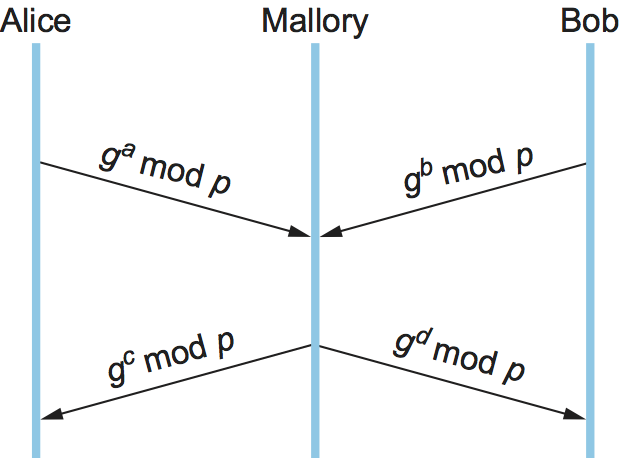
Fixed DH relies on certificates that are similar to public key certificates but instead certify the Diffie-Hellman public parameters of an entity. This, for example, authenticates a web server before sending a CC.
---
Tags:
#lit
Reference:
[[@IllustratedTLSConnection]]
[[@vaccaComputerInformationSecurity2013]]
[[@petersonComputerNetworksSystems]]
Related:
[[Detailed walkthroughs of computer protocols]]