- Understanding Incident Analysis in a Threat-Centric SOC
- ****[**7.1 **Introduction ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/1)
-
- ****[**7.2 **Classic Kill Chain Model Overview ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/2)
- the process by which a threat actor would build a plan or strategy to affect a specific goal or end-state against a target. The kill chain is part of an intelligence-driven defense model that is used to identify, detect, and prevent intrusions by threat actors. Attacks and threats can be stopped or prevented at any point in the kill chain.
- ****[**7.3 **Kill Chain Phase 1: Reconnaissance ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/3)
-
- ****[**7.4 **Kill Chain Phase 2: Weaponization ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/4)
- develop a cyber weapon that is based on reconnaissance information about a targeted system, which has pre-determined objectives when deployed. The designers of the weapon decide on the specific vulnerabilities to be exploited based on the vulnerabilities of the targets that are discovered during reconnaissance.
- ****[**7.5 **Kill Chain Phase 3: Delivery ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/5)
- Delivery can be accomplished by some of the following methods:
- Email attachments
- Phishing emails
- Directing individuals to websites
- USB devices
- ****[**7.6 **Kill Chain Phase 4: Exploitation ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/6)
- The three typical weaknesses are:
- Applications
- Operating system vulnerabilities
- Users
- ****[**7.7 **Kill Chain Phase 5: Installation ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/7)
- Persistence such as surviving reboots or av
- ****[**7.8 **Kill Chain Phase 6: Command-and-Control ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/8)
- C2 channel
- ****[**7.9 **Kill Chain Phase 7: Actions on Objectives ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/9)
- the threat actor's actions are objective-dependent, such as intellectual property theft, corporate data theft, bandwidth theft for spam, and distributed DoS traffic, or use of the target machine as part of a bot-net to rapidly generate digital currency, which is where the hacker achieves their ultimate goal. Anther is encrypting with ransomware.
- ****[**7.10 **Applying the Kill Chain Model ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/10)
- ****[**7.11 **Diamond Model Overview ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/11)
- Adversary, Victim, Infrastructure, Capabilities
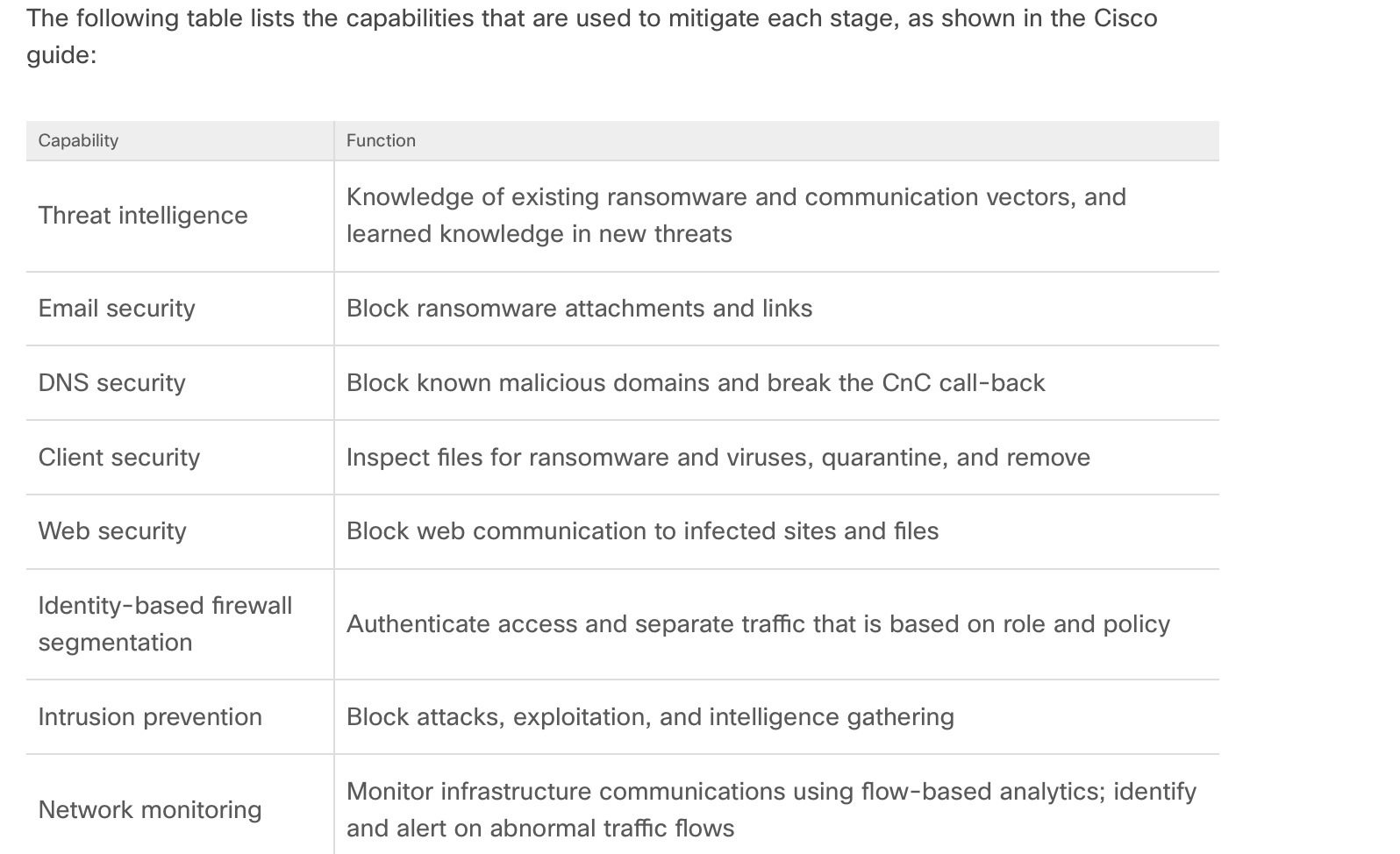
- ****[**7.12 **Applying the Diamond Model ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/12)
- 
- **Type 1 infrastructure** is owned and controlled by the adversary.
- **Type 2 infrastructure **is co-opted by the adversary, but is owned by a third party that may or may not know that the adversary is using the infrastructure. The true identity of the adversary is obfuscated. The attacker gains access to a target solely for "hopping” through during an attack. To the target it would appear as if the attack came from the intermediary “hop,” and cloak the attacker’s true identity.
- **Service providers** are the entities that provide type 1 and type 2 infrastructures and include entities such as an ISP. Most access to the Internet is provided through an ISP, both privately for home use and commercially to businesses.
- ****[**7.13 **MITRE ATTACK™ Framework ](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/13)
- Preattack, mobile, cloud, enterprise, scada
- ttps(tools techniques procedures) at higher level than iocs
- Not all SOCs are equal
- ****[**7.14 **Investigate Hacker Methodology](https://ondemandelearning.cisco.com/cisco/cbrops10/sections/7/pages/14)