- Understanding Network Infrastructure and NSM Tools
- Intro
- No standard set of Tools, typically fulfill a need. SO is one.
- NAT Fundamentals
- 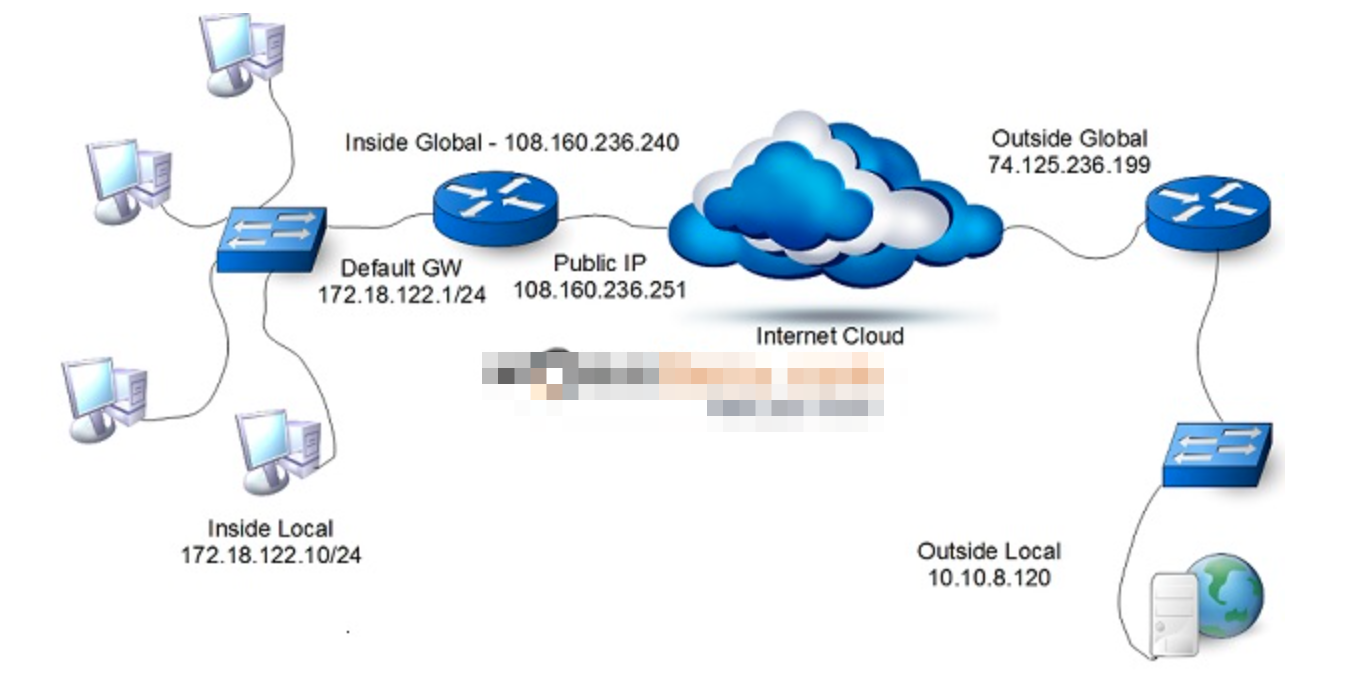
- **Static NAT:** This deployment choice maps an unregistered IPv4 address to a registered IPv4 address. One-to-one static NAT is particularly useful when a device must be accessible from outside the network. For example, static NAT is used when a server on a DMZ needs to be continuously reachable by the same predictable, translated address.
- **Dynamic NAT:** This deployment choice maps an unregistered IPv4 address to a registered IPv4 address from a pool of registered IPv4 addresses which is useful for outbound client connections when you have fewer outside global IP addresses than inside local hosts.
- **Dynamic Port Address Translation (PAT):** This deployment choice maps multiple unregistered IPv4 addresses to a single registered IP address by using the source port to distinguish between translations. That single IP address may be the IP address of the NAT device itself. Different systems may refer to dynamic PAT using different terms. Examples include NAT overload, Hide NAT and Many to One NAT.
- **Static PAT:** Imagine a network which has just one single public IP address. This IP address must be used by the firewall that connects the network to the Internet. It must also be used as the PAT address for all outbound connections. If this network must also support a DMZ server, then Static PAT can be used. For example, TCP port 80 may be reserved for PAT translation to the HTTP service on the DMZ server. Static PAT is sometimes called port forwarding.
- **Policy NAT:** This deployment choice uses extended criteria, such as source addresses, destination addresses, and transport layer ports to specify the translation. For example, traffic that is destined to a particular partner network may be translated to a specific address using PAT while traffic destined elsewhere is translated using a dynamic NAT pool.
- Packet Filtering with ACLs
- ACLs can be used for various functions on a Cisco IOS router. For example, they can be used to classify which packets are permitted into a priority queue. They can be used to classify which networks an OSPF process will advertise or which network advertisements an OSPF process will accept. They can be used to classify which packets will have their forwarding path specified by a policy-based route.
- When an ACL is applied to an interface with the **access-group** command, it implements a packet filter. Referring to the topology that is depicted above, consider the following ACL applied to the gi0/1 interface in the inbound direction:
- There is an explicit deny for all other packets as the last entry in the ACL. While this line is not required to deny all packets that were not matched by earlier entries, it does serve two purposes. First, hit counters are maintained for each line in the ACL. The administrator can use the **show access-list 100**command to view the ACL and each entry’s hit count. Without the explicit deny, there would be no record of the number of packets that were denied by the ACL.
- The default though is an IMPLICIT deny.
-
- ACLs with the Established Option
- the **established** keyword requires that either the ACK bit or the RST bit to be set in the TCP flags of a packet. (With two nets it can allow initiations to the other net by only one of the nets)
- the last thing to point out in this scenario is an example of a limitation of relying on packet filters that reference the TCP flags in the TCP header of packets. Imagine the attacker in the topology wants to start reconnaissance by mapping out the IP addresses of hosts on the trusted side of the packet filter. Note that the ACL will not permit ping via ICMP echo requests. The attacker can, however, make clever use of an “ACK scan.” Instead of sending an ICMP echo request, the attacker can send a TCP packet with the ACK bit set to a destination address. Since the ACK bit is set, these packets will match the **established**keyword reference in the ACL and will be permitted. If there is a host present, that host will respond with a TCP reset (a TCP packet with the RST bit set) in response. The attacker can perform the same sort of reconnaissance as it could with ICMP ping.
- Access Control Models
- Uses an ACL to decide which users or group of users have access to the information. The owner of information is able to change the ACL permissions at his discretion.
- Discretionary access control
- ********
- Access decisions are based on an individual's roles and responsibilities within the organization, also known as role-based access control (RBAC).
- Non-discretionary access control
- ********
- Secures information by assigning sensitivity (security level) labels on information and comparing them to the level of sensitivity that a user is operating at. Usually appropriate for extremely secure systems, such as military applications or mission critical applications.
- Mandatory access control
- Time, Rule, Context multi-channels, Attribute (next gen)
- Authentication, Authorization and Accounting
- **Authentication** identifies a user before allowing the user access to the network.
- **Authorization:** Defines what an individual or groups of identities are allowed to do once authenticated
- **Accounting:** Keeps track of what individual identities have done.
- In all but the smallest deployments, centralized AAA is preferred over local AAA. With centralized AAA, configuration and maintenance of AAA policy is more manageable. Authentication and authorization methods are defined and managed centrally and made available to all devices in the network. Beyond the initial configuration, maintenance is also simplified. If an authorization policy is changed in the centralized system, the change is inherited by all devices. Centralized AAA also enables the use of the Accounting method. Accounting records from all devices are sent to centralized repositories enabling simplified auditing of accounting records.
- Scalability and routers generally can't support extended accounting
- LDAP, RADIUS, TACACS+
- 1812/1813/1645/1646 RADIUS, only encrypts pwd, other comm in the clear, no accounting in AAA
- 49 TACACS, encrypts everything, full AAA
-
- Load Balancing
- **Round robin:** Requests are distributed across the group of servers sequentially.
- **Least connections: **A new request is sent to the server with the fewest current connections to clients.
- **Least time:** Requests are sent to the server according to a formula that combines the fastest response time and fewest active connections.
- **Hash:** Requests are distributed based on a hash value, such as the source and destination IP address.
- Most current-generation WAFs use two techniques for threat detection: signature-based pattern matching and signature-less techniques. Signature-less techniques to detect unknown zero-day threats include behaviors, machine learning, and artificial intelligence (AI).
- WAFs make web-based attacks easier, faster, less complex
- Network-Based Malware Protection
- 40% effective, also uses centralized cloud database.
- Using network-based malware protection, configured policy can select file types to monitor over commonly used protocols and send the SHA-256 hashes, metadata from the files, or even copies of the files themselves to the cloud for analysis.
- Cisco Collective Security Intelligence Cloud and Cisco Firepower NGIPS - nextgen ips
- Trajectory of detections
- NSM Tools
- commercial have support but cost more. Free tend to also offer support contracts. Homegrown tools scripted/programmed.
- Example of syslog:
- Receiving syslog messages from syslog clients that are distributed across the network, and storing those messages in a flat log file
- Moving messages from the flat log file to a high-performance relational database
- Processing low-level data in the relational database to produce higher-level information constructs
- Presenting syslog data in the form of automated reports, dashboards, and real-time query responses