- Ch 1 Defining the SOC
- Centralized command center for NSM, detect analyze report.
- threat-centric, compliance, operational
- focuses on addressing security across the entire attack continuum—before, during, and after an attack. (threat-centric SOC)
- focuses on comparing the posture of network systems to reference configuration templates or standard system builds. (compliance-based SOC)
- monitors the security posture of an organization’s internal network. (operational-based SOC)
- Tools
- Security Onion, ELK, Snort/Suricata (NIDS/NIPS), Bro, OSSEC, Netsniff-ng, sysmon, syslog-ng. SOnion: NetworkingMiner, Sguil console, Cyberchef, capme.
- Data analytics is the science of examining and deciphering raw data or data sets with the purpose of drawing conclusions. A data set is a collection of related, discrete items of related data in a structure that may be accessed individually, in combination, or managed as a whole entity
- Dynamic analysis is the testing and evaluation of a program by executing the data in real time to find errors (malware analysis)
- **Predictive** analysis can be used to **make** **predictions** **about** **unknown** **future** **attacks** or **events**.
- Log mining
- **Sequencing:** Reconstructing or following the network traffic flow.
- **Path analysis:** An interpretation of a chain of consecutive events that occur during a set period. Path analysis is a way to understand an attacker’s behavior to gain actionable insights into log data.
- **Log clustering:** Used to mine through large amounts of log data to build profiles and to identify anomalous behavior.
- A NetFlow analyzer can also help with incident response by providing context visibility for IP conversations.
- Automate as much as possible. Ticket generation, Compare with Common Vulnerabilities and Exploits, SOC reports to mgmt.
- Anomaly detection can be a more complex process for detecting an attack than a simple signaturealert. Some tools have the ability to generate anomaly alerts based on either volume or featurepatterns. Volumebased alerts can come from statistical analysis, frequency, and time series forecasting.
- Feature-based anomaly alerts can be a lot more intensive and time-consuming to set up andimplement.
- Anomaly/statistical/volume ex. Bro detecting SMTP t raffic on a webhost. Hadoop for big data mining.
- By integration and correlating alarms and events with data from threat intelligence, SIEMs, and other security analytics tools, alarm prioritization can be automated at machine speed. Effective prioritization relieves SOC Tier 1 analysts from the labor-intensive task of sorting through tens of thousands of low-level and irrelevant alerts each day. (Cisco Firepower)
- 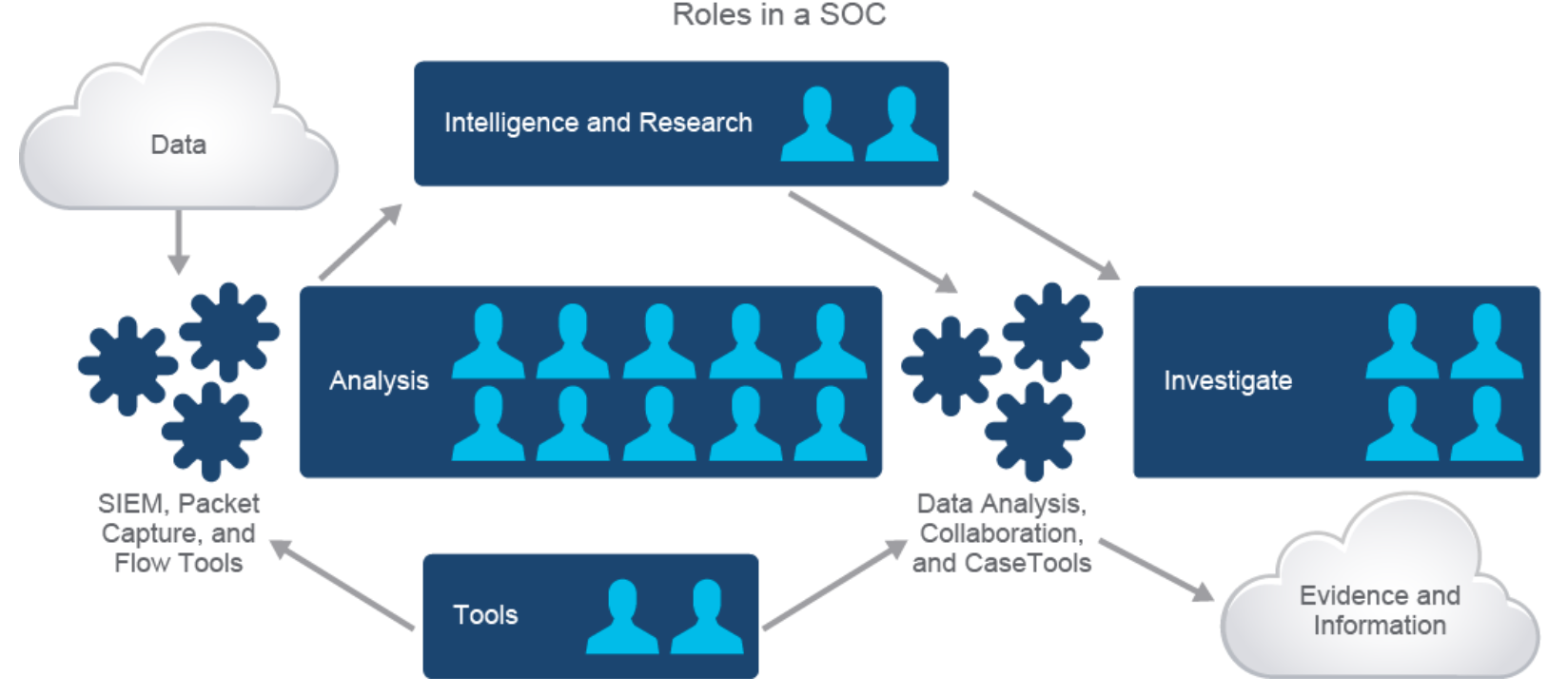
- This SOC job role diagram is not specific because research has indicated that organizations vary widely on the job roles and responsibilities within a SOC.
- Roles
- SOC Manager: prioritization and organization, develop workflow and SOPs
- T3: In-depth technical knowledge, develop tune and implement threat detection analytics. Hunter.
- T2: Deep-dive incident analysis. Advised on remediation and new analytic methods.
- T1: Monitors alert queue and triages alerts. Device health, collects data for T2.
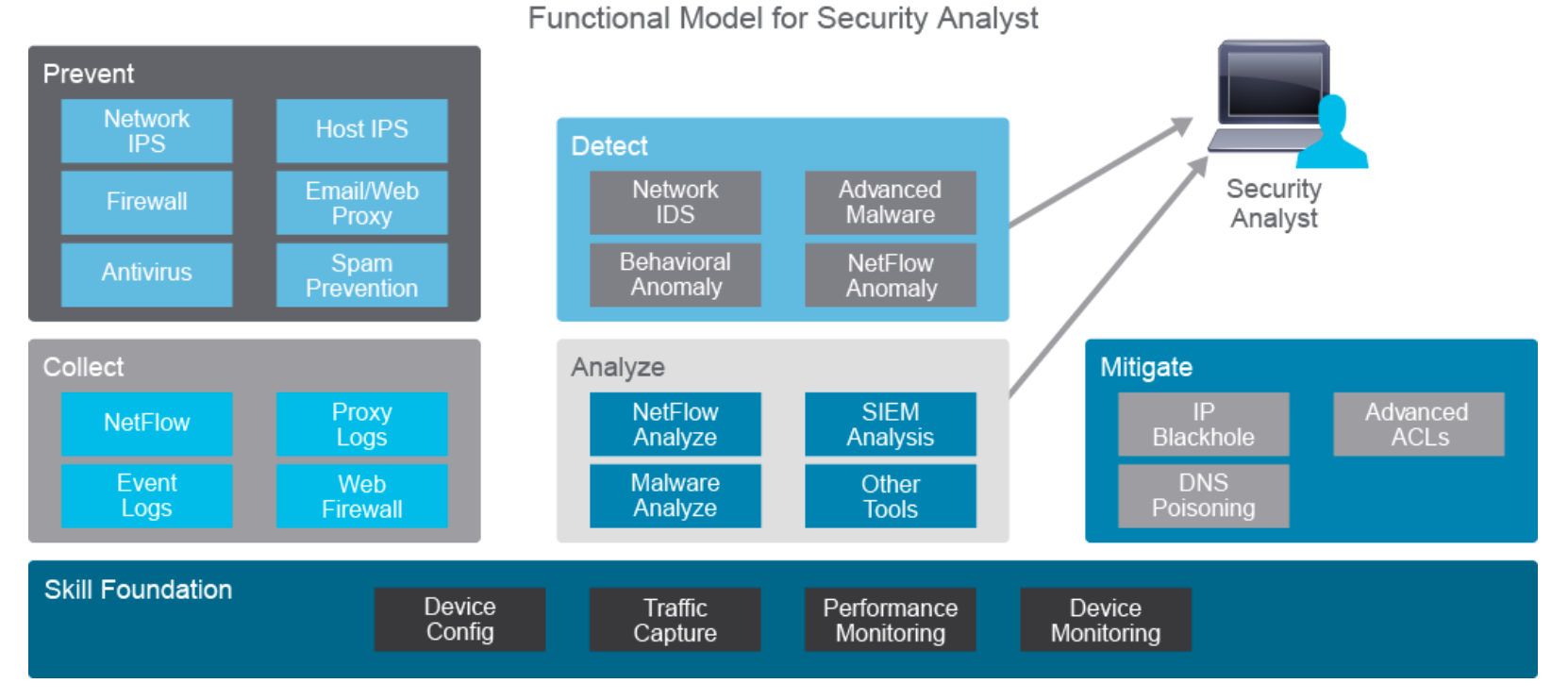
- 
- Outside orgs
- Cisco Talos
- US-CERT
- FIRST
- Malwr
- CVE
- Payload Security
- PhishTank
- Introduction
- Types of SOCs
- SOC Analyst Tools
- DAta Analytics
- Hybrid installs: Automated Reports, Anomaly Alerts
- Staffing and Effective Incident Response Team
- Roles in a SOC
- Developing Key Relationships with External Resources